The following code below compares adjacent cells in 2 column's (D and E) and colors only those cells in column E that have a different data than column D :
Sub validateFields()
Dim dColumn As Variant
Dim eColumn As Variant
Set dColumn = Range("D:D")
Set eColumn = Range("E:E")
Dim cellIndex As Integer
cellIndex = 2
Do While dColumn.Cells(cellIndex).Value <> ""
If dColumn.Cells(cellIndex) <> eColumn.Cells(cellIndex) Then
With eColumn.Cells(cellIndex).Interior
.ColorIndex = 36
.Pattern = xlSolid
End With
Else
With eColumn.Cells(cellIndex).Interior
.ColorIndex = 0
.Pattern = xlSolid
End With
End If
cellIndex = cellIndex + 1
Loop
End Sub
Private Sub Worksheet_Activate()
Call validateFields
End Sub
This assumes that the first column has the header, so, ignores it.
(cellIndex = 2 initialization)
Tuesday, December 12, 2006
Tuesday, November 28, 2006
View thumbnails on Windows!!
If due to some reason if the thumbnails can not be viewed on your system, which happens mainly because of installing a new application on Windows 2000, say, then you can use the below registry fix. Just copy paste it on to a new notepad, save it as .reg and then just double click on it to apply.
REGEDIT4
[HKEY_CLASSES_ROOT\.gif]
[HKEY_CLASSES_ROOT\.gif\ShellEx]
[HKEY_CLASSES_ROOT\.gif\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.jpg]
[HKEY_CLASSES_ROOT\.jpg\ShellEx]
[HKEY_CLASSES_ROOT\.jpg\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.art]
[HKEY_CLASSES_ROOT\.art\ShellEx]
[HKEY_CLASSES_ROOT\.art\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.bmp]
[HKEY_CLASSES_ROOT\.bmp\ShellEx]
[HKEY_CLASSES_ROOT\.bmp\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.dib]
[HKEY_CLASSES_ROOT\.dib\ShellEx]
[HKEY_CLASSES_ROOT\.dib\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.jpe]
[HKEY_CLASSES_ROOT\.jpe\ShellEx]
[HKEY_CLASSES_ROOT\.jpe\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.jpeg]
[HKEY_CLASSES_ROOT\.jpeg\ShellEx]
[HKEY_CLASSES_ROOT\.jpeg\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.png]
[HKEY_CLASSES_ROOT\.png\ShellEx]
[HKEY_CLASSES_ROOT\.png\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.tif]
[HKEY_CLASSES_ROOT\.tif\ShellEx]
[HKEY_CLASSES_ROOT\.tif\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.tiff]
[HKEY_CLASSES_ROOT\.tiff\ShellEx]
[HKEY_CLASSES_ROOT\.tiff\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.wmf]
[HKEY_CLASSES_ROOT\.wmf\ShellEx]
[HKEY_CLASSES_ROOT\.wmf\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
Just refresh for the changes to apply!!
REGEDIT4
[HKEY_CLASSES_ROOT\.gif]
[HKEY_CLASSES_ROOT\.gif\ShellEx]
[HKEY_CLASSES_ROOT\.gif\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.jpg]
[HKEY_CLASSES_ROOT\.jpg\ShellEx]
[HKEY_CLASSES_ROOT\.jpg\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.art]
[HKEY_CLASSES_ROOT\.art\ShellEx]
[HKEY_CLASSES_ROOT\.art\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.bmp]
[HKEY_CLASSES_ROOT\.bmp\ShellEx]
[HKEY_CLASSES_ROOT\.bmp\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.dib]
[HKEY_CLASSES_ROOT\.dib\ShellEx]
[HKEY_CLASSES_ROOT\.dib\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.jpe]
[HKEY_CLASSES_ROOT\.jpe\ShellEx]
[HKEY_CLASSES_ROOT\.jpe\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.jpeg]
[HKEY_CLASSES_ROOT\.jpeg\ShellEx]
[HKEY_CLASSES_ROOT\.jpeg\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.png]
[HKEY_CLASSES_ROOT\.png\ShellEx]
[HKEY_CLASSES_ROOT\.png\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.tif]
[HKEY_CLASSES_ROOT\.tif\ShellEx]
[HKEY_CLASSES_ROOT\.tif\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.tiff]
[HKEY_CLASSES_ROOT\.tiff\ShellEx]
[HKEY_CLASSES_ROOT\.tiff\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
[HKEY_CLASSES_ROOT\.wmf]
[HKEY_CLASSES_ROOT\.wmf\ShellEx]
[HKEY_CLASSES_ROOT\.wmf\ShellEx\{BB2E617C-0920-11d1-9A0B-00C04FC2D6C1}]
@="{7376D660-C583-11d0-A3A5-00C04FD706EC}"
Just refresh for the changes to apply!!
Friday, November 17, 2006
Converting Float to Double in a not so common way!!!!
I was working on a project and i had this strange but common problem. I was getting a value from an external system which was a primitive float. But, in our system it was all double. I had to convert the float to double without losing any precision. I tried to cast it directly into double but it didn't work. As, say, for example, if i was trying to convert 39.355F to double, then it turned out to be 39.35497... It always used to change the precision and in my case i didn't want it to change due to some processing i would be doing on it later. You could say i could have just rounded it off, but, in my case it wouldn't work. So, here i found a nice cute way to convert float to double as it is with out change in even a single digit also. It may seem it is not needed but believe me some times this all you can do. At least, this is what i could figure out when deadline was on my head.
public static double floatToDouble (float converThisNumberToFloat) {
String floatNumberInString = String.valueOf(converThisNumberToFloat);
double floatNumberInDouble = Double.parseDouble(floatNumberInString);
return floatNumberInDouble;
}
public static double floatToDouble (float converThisNumberToFloat) {
String floatNumberInString = String.valueOf(converThisNumberToFloat);
double floatNumberInDouble = Double.parseDouble(floatNumberInString);
return floatNumberInDouble;
}
Thursday, November 16, 2006
Some usefull registry tweaks for developer!
To get command prompt on the right click:
1. Open regedit.exe from Run menu
2. Navigate to
HKEY_LOCAL_MACHINE/Software/Classes/Folder/Shell
and create a key called "Command Prompt".
3. Set the default string to "Command Prompt" or simply "CMD", since this text will come when you right click on a FOLDER.
4. Create a new key within the newly created command prompt named "command," and set the default string to
cmd.exe /k pushd %L
5. Refresh By pressing F5.
PS: This works on NT based System. Also, the right click should be on a FOLDER. If you open the folder and the click on the screen area, then it won't work.
To Get Tabbed browsing in Command Prompt:
1. Open regedit.exe from Run menu
2. Navigate to
HKEY_LOCAL_MACHINE/SOFTWARE/Microsoft/Command Processor
3. Set PathCompletionChar = 0X9
4. Set CompletionChar = 0X9
PS: 0X9 is Hex digit 9.
1. Open regedit.exe from Run menu
2. Navigate to
HKEY_LOCAL_MACHINE/Software/Classes/Folder/Shell
and create a key called "Command Prompt".
3. Set the default string to "Command Prompt" or simply "CMD", since this text will come when you right click on a FOLDER.
4. Create a new key within the newly created command prompt named "command," and set the default string to
cmd.exe /k pushd %L
5. Refresh By pressing F5.
PS: This works on NT based System. Also, the right click should be on a FOLDER. If you open the folder and the click on the screen area, then it won't work.
To Get Tabbed browsing in Command Prompt:
1. Open regedit.exe from Run menu
2. Navigate to
HKEY_LOCAL_MACHINE/SOFTWARE/Microsoft/Command Processor
3. Set PathCompletionChar = 0X9
4. Set CompletionChar = 0X9
PS: 0X9 is Hex digit 9.
Friday, November 10, 2006
Anonymity in Code too not allowed!
So, here i go into the java world. The only world which am into presently. You write code, tons of java code. There area few who would not like to give there source code to other. As, they feel that its there work, they have put lots of hour of effort into it, have optimized the code to the maximum extent possible and why should some other guy with very little effort get to know what they have done. So, if you think you can just provide the class file to them and not the source java file, again you are wrong. Reverse-engineering is present in this world, and this applies to java code too. You just have to input the class file to the tool and with in few seconds the whole source is at your disposal. I found 3 tools which did the same, two free and one paid.
I will start from the least user friendly one.
1. The javap tool that comes with the JDK itself. This is a command line tool. But, the decompiled code is not too easy to follow. I tried it with all the command line options present. I wouldn't suggest this tool unless you really want to know the whole inside of the code, i mean at the byte code level.
2. The next tools is also a free tool, Cavaj. This is really cool, and much more easier to use than the ugly command line version of the javap. You just have to open the class file and the Cavaj does the rest. The exact java file is back on your screen. With not much options present like syntax coloring or finding matching braces, this tool serves the purpose. Once you have decompiled you can use some other IDE like eclipse to do the remaining part of your work on the code you just decompiled.There is one more platform independent version JCavaj in java.
3. The last tool i went through was DJ Decompiler. Now this isn't a freeware, and does the same job as the one above but has much more options like syntax coloring, getting the byte code version of the decompiled code, searching matching parenthesis, running the applet, compiling the code from the GUI itself, shell integration so that you can right click the class file and decompile and some more. But, all these comes with a cost.
I personally liked the DJ decompiler and would suggest to bye it if you have enough money, but the basic purpose of the Decompiling is achieved in a good manner using the CavaJ decompiler, Which also gets a thumbs up from my side.
I will start from the least user friendly one.
1. The javap tool that comes with the JDK itself. This is a command line tool. But, the decompiled code is not too easy to follow. I tried it with all the command line options present. I wouldn't suggest this tool unless you really want to know the whole inside of the code, i mean at the byte code level.
2. The next tools is also a free tool, Cavaj. This is really cool, and much more easier to use than the ugly command line version of the javap. You just have to open the class file and the Cavaj does the rest. The exact java file is back on your screen. With not much options present like syntax coloring or finding matching braces, this tool serves the purpose. Once you have decompiled you can use some other IDE like eclipse to do the remaining part of your work on the code you just decompiled.There is one more platform independent version JCavaj in java.
3. The last tool i went through was DJ Decompiler. Now this isn't a freeware, and does the same job as the one above but has much more options like syntax coloring, getting the byte code version of the decompiled code, searching matching parenthesis, running the applet, compiling the code from the GUI itself, shell integration so that you can right click the class file and decompile and some more. But, all these comes with a cost.
I personally liked the DJ decompiler and would suggest to bye it if you have enough money, but the basic purpose of the Decompiling is achieved in a good manner using the CavaJ decompiler, Which also gets a thumbs up from my side.
Thursday, November 09, 2006
Nope, you can't hide anything on LAN tooo... LOL
I found this one more cool software called LanSpy. You can use this tool to get the information about systems present on the LAN. There are some other tools similar to this, but, i found this rather simple to use. So, for a new bee, this tool is good to start. All, the various tools present to know about the network or your LAN has been integrated very neatly in this software. All the ports which are open are listed, also, the programs or services that are using this is also displayed.
Using this tool you can get the Domain name, NetBios name, MAC address to name a few.
The most interesting part of the software is its ability to display the process and the servicess running on the remote system. It also displays the user accounts present on that system, registry with the hotfixes that have been applied to that system. Also, it gives us the list of password policy applied for that system, the roles that are applied to that system, logged users, the groups present and more.
Basically, a very good tool you can start with if you know some fundamental things about the networking.
And again it a Free Tool!!!
http://lantricks.com/lanspy/
There are some more advanced tools present on the net that allows you to do more(Only for advancd users!!!). Say for example, you can start & stop process on that machine!! great ! But, some softwares i came across were paid softwares like LAN Inventory 1.0. Will let you all know if i ever find some free softwares which does that!!
Using this tool you can get the Domain name, NetBios name, MAC address to name a few.
The most interesting part of the software is its ability to display the process and the servicess running on the remote system. It also displays the user accounts present on that system, registry with the hotfixes that have been applied to that system. Also, it gives us the list of password policy applied for that system, the roles that are applied to that system, logged users, the groups present and more.
Basically, a very good tool you can start with if you know some fundamental things about the networking.
And again it a Free Tool!!!
http://lantricks.com/lanspy/
There are some more advanced tools present on the net that allows you to do more(Only for advancd users!!!). Say for example, you can start & stop process on that machine!! great ! But, some softwares i came across were paid softwares like LAN Inventory 1.0. Will let you all know if i ever find some free softwares which does that!!
Wednesday, November 08, 2006
Are you showing off to be invisible?? LOL
Today, while I was browsing the internet I found this cool software called 'Buddy Spy'. I got my hand on the version 2.2. It has been written in VB6 and believe me, Its a Job well done. This software allows you to see what other yahoo messenger users are doing or pretending to do. he he he...Are they in stealth mode or if they are chatting in a chat room with a busy status message!! Also, if they have a web cam and if its online. It uses the YMSG protocol.
It has a really cool GUI. Now, let me take you through the steps to know the Unknown!!!
After installation when you launch the application, it comes up with a welcome screen, With news alerts, if any. You can navigate by clicking on the links present on the left hand side to different sections.
Then comes the configure section. Here you can give the username and password to log into yahoo and select various parameters like the yahoo server you want to log into, web cam server etc.
You can show your status to be invisible or even a custom message.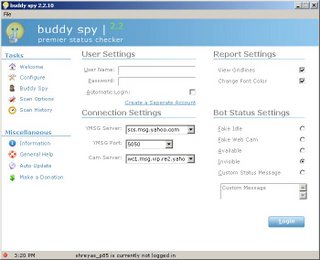

Next comes the 'buddy spy' screen. Here you can specify the name of the user to see his real status. You have to log in first to check these status. You can even see the chat rooms he is chatting in, if any!!! You can scan for a single user or you can provide a list of names to scan at once! Too cool! There are many more setting to fine tune the way the buddy searches on the yahoo server.
And most importantly its FREE FREE FREEEEE..... :) :)
It has a really cool GUI. Now, let me take you through the steps to know the Unknown!!!
After installation when you launch the application, it comes up with a welcome screen, With news alerts, if any. You can navigate by clicking on the links present on the left hand side to different sections.
Then comes the configure section. Here you can give the username and password to log into yahoo and select various parameters like the yahoo server you want to log into, web cam server etc.
You can show your status to be invisible or even a custom message.


Next comes the 'buddy spy' screen. Here you can specify the name of the user to see his real status. You have to log in first to check these status. You can even see the chat rooms he is chatting in, if any!!! You can scan for a single user or you can provide a list of names to scan at once! Too cool! There are many more setting to fine tune the way the buddy searches on the yahoo server.
And most importantly its FREE FREE FREEEEE..... :) :)
Tuesday, November 07, 2006
Access internet with total anonymity - 2
Tor is also a free software available and is used to protect privacy of the users. Users can communicate anonymously over the internet using tor. There is a proxy running on your local system. All the application which need anonymous access to the out side net have to use this proxy. The proxy server connects to the tor network, and periodically created virtual circuit through the tor network. The proxy is also called onion proxy for the way in which the cryptography is implemented, in a layered fashion, like that of the onion. Software provides a SOCKS interface to the clients. Applications that can use SOCKS can be pointed at the Tor, which can then route the traffic through the virtual circuit created in the Tor network.
This Tor is often used with Privoxy, I had introduced before. The Tor works at the TCP layer while the privoxy works at the application layer. You can point to 'localhost:9050' to use Tor directly with application, or you can point at 'localhost:8118' to use it with privoxy.
This Tor is often used with Privoxy, I had introduced before. The Tor works at the TCP layer while the privoxy works at the application layer. You can point to 'localhost:9050' to use Tor directly with application, or you can point at 'localhost:8118' to use it with privoxy.
Monday, November 06, 2006
Access internet with total anonymity - 1
There are 2 free tools available on the internet using which you can be totally anonymous in the internet.
The first one I would like to describe is Privoxy:
Now this is a web proxy. Instead of connecting to the server directly, we can connect to this web proxy. This will get all the webpages from the server instead of we getting them by contacting the server directly. Let me make it clear that am not advertising these software's, but only suggesting them from my own knowledge and experience.Privoxy helps for privacy protection and also add and junk filtering. This feature of add filtering is what impressed me the most. Also, you can setup the privoxy as a server on a local lan and redirect all the machines to this server to serve the request.You can use it also as a service in WinNT based systems. And now you can use this with another r type of proxies called transparent proxy, these can run on default http port 80. I will give an intro to Tor next.
WebPage: http://www.privoxy.org/
Some usage details:
Uses port: 8118
Configuration at: http://p.p/
To set up as a server on Lan : In the main configuration file 'listen-address' option, uncomment it. Assign it the address of the LAN gateway interface, and port number to use.
Will speak about Tor next time..
The first one I would like to describe is Privoxy:
Now this is a web proxy. Instead of connecting to the server directly, we can connect to this web proxy. This will get all the webpages from the server instead of we getting them by contacting the server directly. Let me make it clear that am not advertising these software's, but only suggesting them from my own knowledge and experience.Privoxy helps for privacy protection and also add and junk filtering. This feature of add filtering is what impressed me the most. Also, you can setup the privoxy as a server on a local lan and redirect all the machines to this server to serve the request.You can use it also as a service in WinNT based systems. And now you can use this with another r type of proxies called transparent proxy, these can run on default http port 80. I will give an intro to Tor next.
WebPage: http://www.privoxy.org/
Some usage details:
Uses port: 8118
Configuration at: http://p.p/
To set up as a server on Lan : In the main configuration file 'listen-address' option, uncomment it. Assign it the address of the LAN gateway interface, and port number to use.
Will speak about Tor next time..
Wednesday, November 01, 2006
A new End!!
Welcome to a new End!!!!
(Every end follows by a new Beginning, so, basically 'Welcome to a new Beginning!!!!' lol)
(Every end follows by a new Beginning, so, basically 'Welcome to a new Beginning!!!!' lol)
Subscribe to:
Posts (Atom)




